
Black-Box Attack Using Neuro-Identifier: Al ubaidy, Mahmood Khalel: 9783330975613: Amazon.com: Books

Security Vulnerabilities of Neural Networks | by Matthew Stewart, PhD Researcher | Towards Data Science

arxiv på Twitter: "Hybrid Batch Attacks: Finding Black-box Adversarial Examples with Limited Queries. https://t.co/00xvLX0ota https://t.co/oul0ht42A7" / Twitter

Sensors | Free Full-Text | A Distributed Black-Box Adversarial Attack Based on Multi-Group Particle Swarm Optimization

Perceptual quality-preserving black-box attack against deep learning image classifiers - ScienceDirect

Proposed method for black-box adversarial attacks in autonomous vehicle... | Download Scientific Diagram
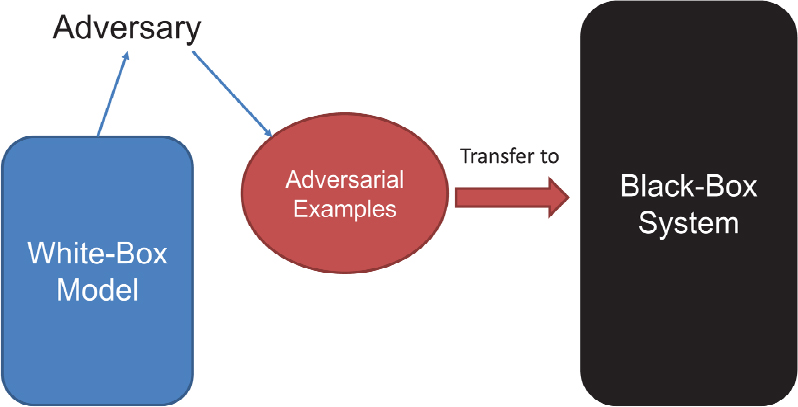
7 Plenary Session | Robust Machine Learning Algorithms and Systems for Detection and Mitigation of Adversarial Attacks and Anomalies: Proceedings of a Workshop | The National Academies Press

FE-DaST: Fast and effective data-free substitute training for black-box adversarial attacks - ScienceDirect

Tricking a Machine into Thinking You're Milla Jovovich | by Rey Reza Wiyatno | Element AI Lab | Medium






![PDF] Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN | Semantic Scholar PDF] Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/86e5827087e11dc929d592ee7b3d7581fc48265e/3-Figure1-1.png)









