Applied Sciences | Free Full-Text | Review of Artificial Intelligence Adversarial Attack and Defense Technologies | HTML
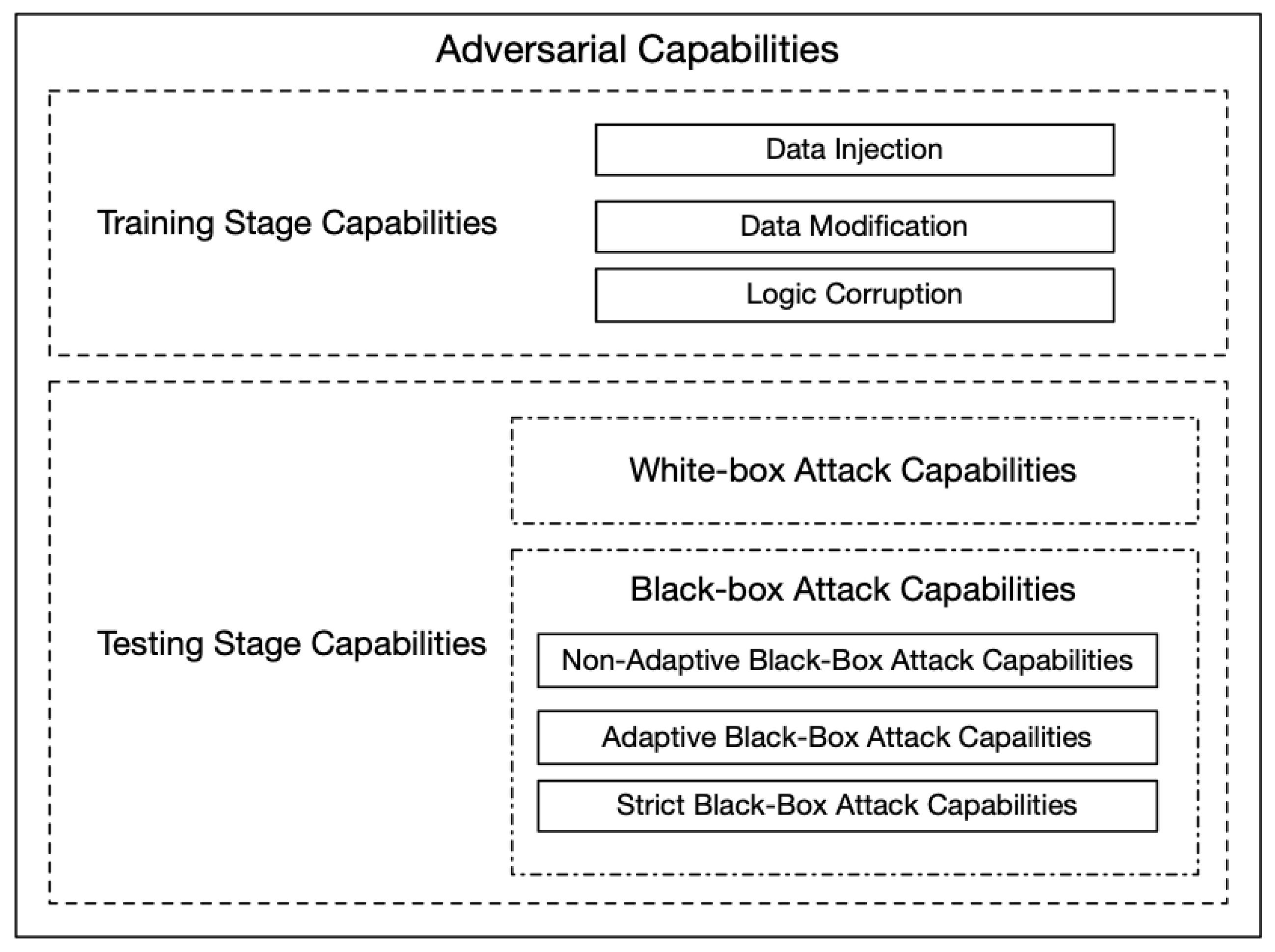
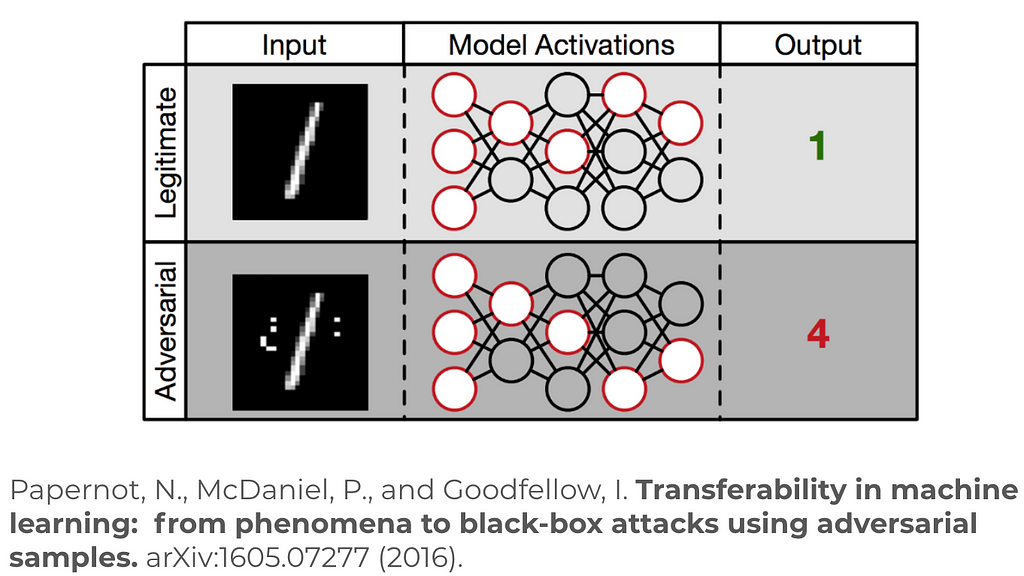
How to attack Machine Learning ( Evasion, Poisoning, Inference, Trojans, Backdoors) | by Alex Polyakov | Towards Data Science
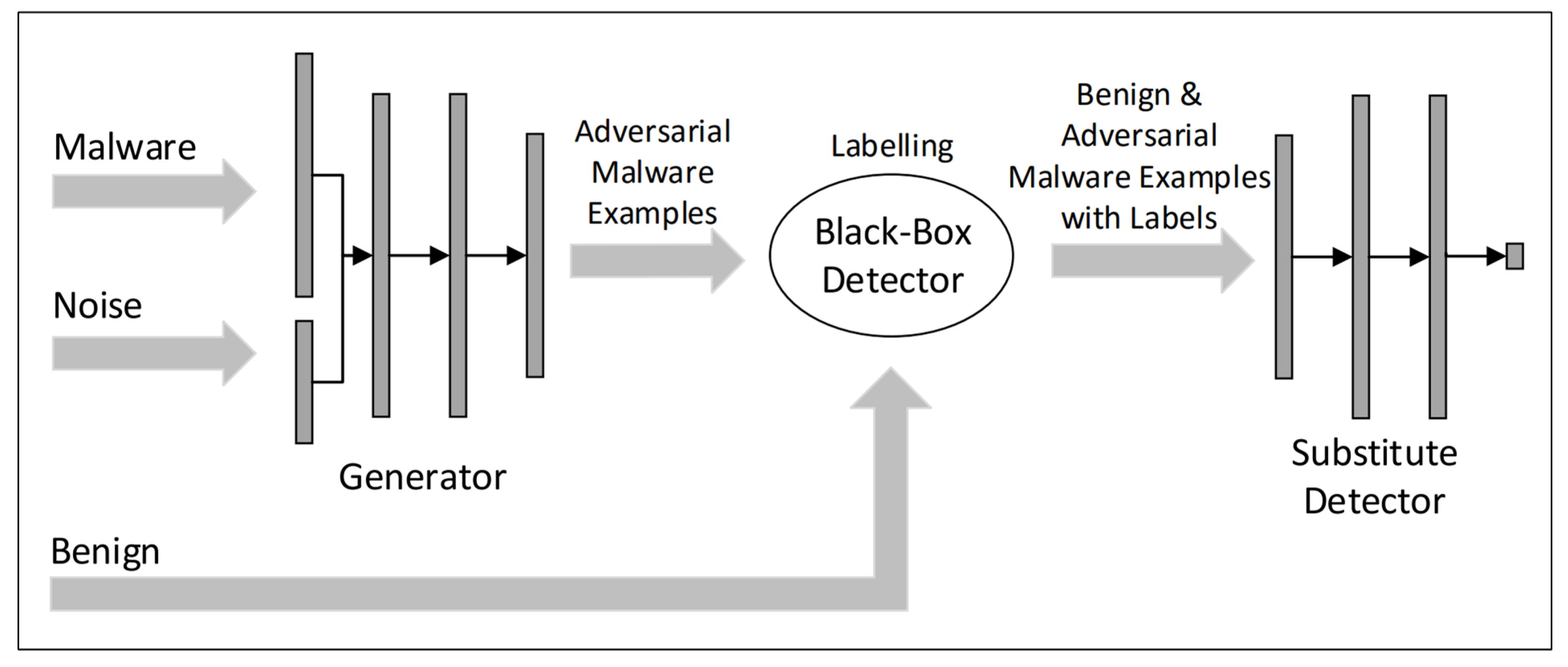
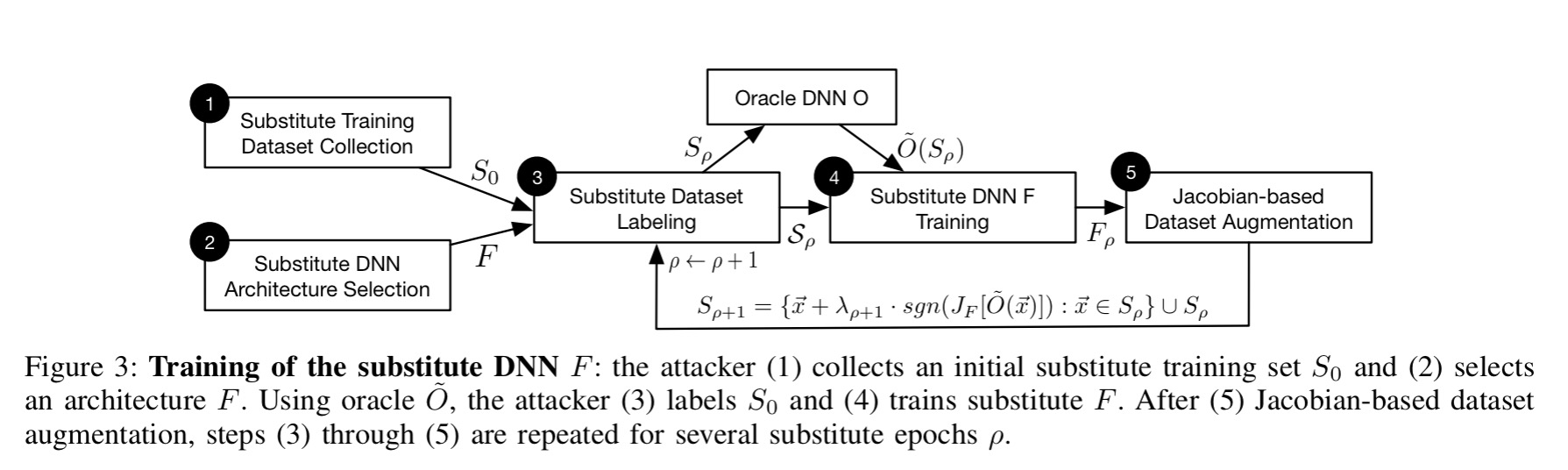
![PDF] Practical Black-Box Attacks against Deep Learning Systems using Adversarial Examples | Semantic Scholar PDF] Practical Black-Box Attacks against Deep Learning Systems using Adversarial Examples | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/94187ef33e34af2cdb42502083c6f9b4c3f5ba6b/5-Figure3-1.png)
PDF] Practical Black-Box Attacks against Deep Learning Systems using Adversarial Examples | Semantic Scholar

![PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b047e503f4c24602f376a774d653f7ed56c024/10-Table2-1.png)







![PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b047e503f4c24602f376a774d653f7ed56c024/10-Figure11-1.png)
![PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b047e503f4c24602f376a774d653f7ed56c024/5-Figure3-1.png)
![PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b047e503f4c24602f376a774d653f7ed56c024/3-Figure2-1.png)
![PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b047e503f4c24602f376a774d653f7ed56c024/12-Figure12-1.png)

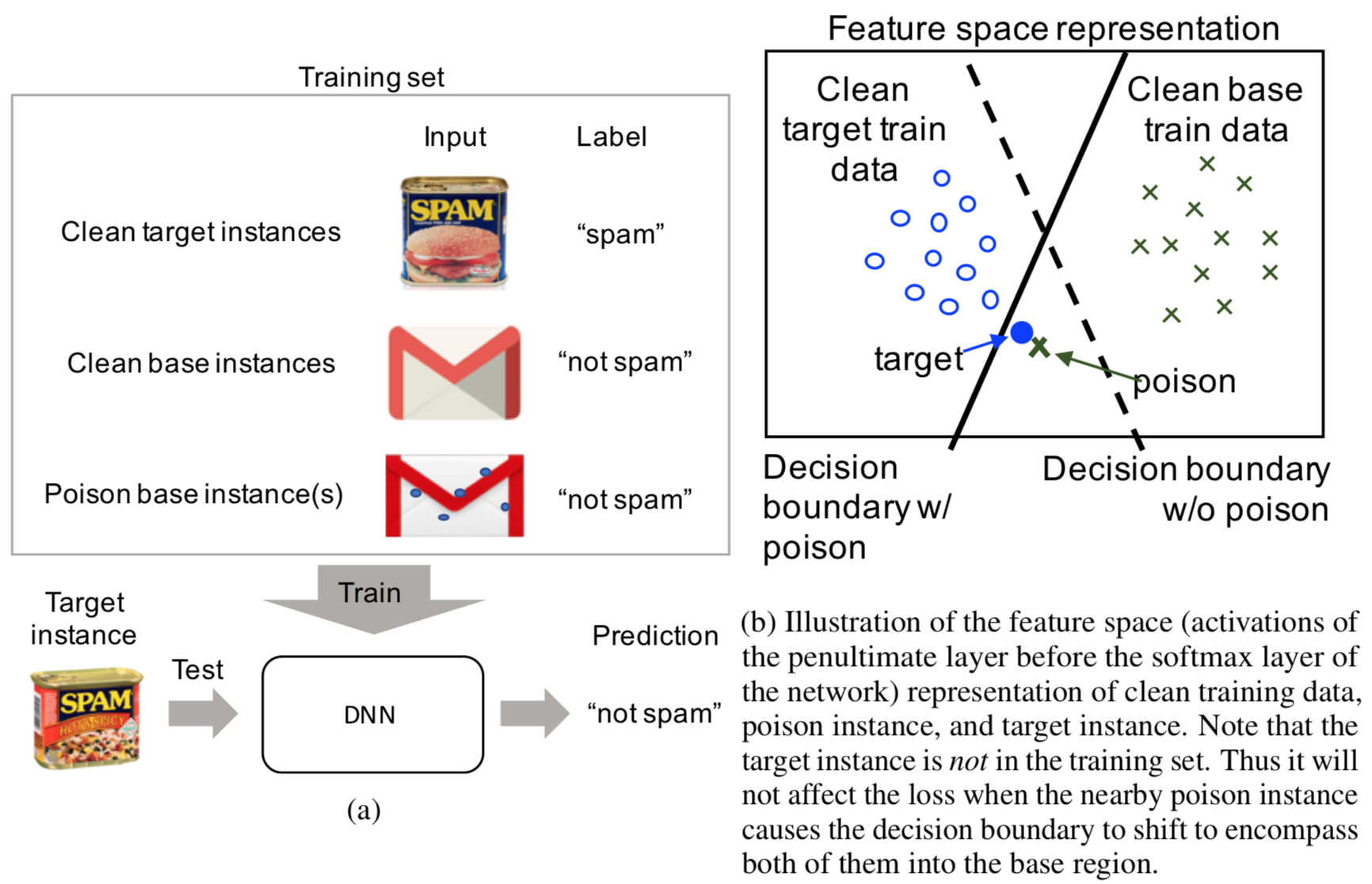

![PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar PDF] Practical Black-Box Attacks against Machine Learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/53b047e503f4c24602f376a774d653f7ed56c024/2-Figure1-1.png)
